3 downloads (last 7 days)
Download Spyware Terminator for Windows and shield your computer with one of the most trusted spyware protection programs available.
Review by Karen M.
Pros
Cons
Welcome to our comprehensive look at Spyware Terminator, the robust defence software tailored for users seeking to protect their systems from malicious spyware. As its principal function, this programme provides real-time protection, a complete scan system, and a user-friendly platform for keeping your computer secure from privacy and performance threats.
What sets Spyware Terminator apart from other anti-spyware software?
Unlike other spyware removal tools, Spyware Terminator prides itself on offering real-time protection against spyware, combined with automatic definition updates to keep your system safeguarded against the latest threats. Its ability to integrate with widely-used antivirus programmes means users benefit from an additional layer of security without the hassle of managing separate security software.
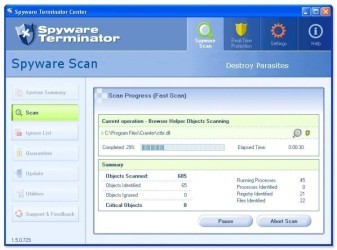
Moreover, the programme has gained considerable merit for its in-depth scanning capabilities, which are both thorough and customisable. Featuring quick, full, and custom scan options, users can tailor their protection to suit their unique needs and schedule scans at convenient times.
Is Spyware Terminator easy to use for non-technical users?
Spyware Terminator has been meticulously designed with a user-friendly interface that facilitates easy navigation for all user levels. Task scheduling and alert systems are intuitive, making it approachable for even those with minimal technical knowledge. The software’s setup wizard and on-screen instructions guide users through the configuration process, ensuring optimal protection with minimal fuss.
Additionally, the support resources offered by Spyware Terminator, including an extensive knowledge base and customer service, empower users to resolve any queries swiftly, further simplifying the user experience.
Does the program support different types of system scans?
Yes, Spyware Terminator is equipped with three types of scanning modes: Quick Scan for rapid checks, Full Scan for an exhaustive system review, and Custom Scan for targeted areas. These options provide flexibility to users looking to conserve time or to delve deeper when the situation necessitates a more comprehensive approach.
Each scan mode is crafted to carry out a detailed analysis of files and folders for potential threats, ensuring a high degree of protection. Users can rest assured that the varied scanning modes cater to different scenarios and needs.
The technical power behind it
Behind its efficient front-end, Spyware Terminator is powered by advanced detection algorithms that help it stay one step ahead of spyware creators. These algorithms are perpetually updated to tackle the latest spyware iterations, demonstrating the programme’s commitment to cutting-edge protection.
The software’s heuristic scanning methodology is particularly noteworthy, capable of preempting potential threats by analysing behavioural patterns that deviate from the norm. This proactiveness serves as a hallmark feature, providing users with a formidable tool against yet-unknown spyware.
Are updates managed effectively within the software?
Absolutely, Spyware Terminator ensures that its users are not burdened by the need to manually handle updates. Instead, automatic updates keep the software’s database current without requiring user intervention, allowing individuals to maintain their focus on their daily computing tasks.
The frequency of these updates corresponds with the evolving threat landscape, confirming that users remain defended against new spyware threats as they emerge.
How does Spyware Terminator stand up against zero-day threats?
The heuristic scanning engine of Spyware Terminator is especially equipped to address zero-day threats. These are emerging spyware threats for which signatures might not yet be available. The software’s behavioural analysis and detection give users an advantage in this critical area of cyber-security.
By identifying and responding to unusual behaviour that may signify a new spyware attack, Spyware Terminator provides proactive defence mechanisms that many similar programs lack.
Tools and utilities included in Spyware Terminator
Not one to rest on its laurels for spyware removal alone, Spyware Terminator is armoured with a suite of additional tools designed to boost system safety and performance. These include an advanced system report feature, which gathers comprehensive information for technical support purposes and a host files checker to protect users from unwanted browser hijacking.
For those looking to safeguard their web surfing experience, the software also comes with an Internet Explorer extension named Web Security Guard, designed to warn users of potentially dangerous websites before they even click on them.
Can users customize the protection settings?
Yes, Spyware Terminator provides a range of configuration options that empower users with control over their protection settings. Customizations include adjustable heuristic levels, scheduled scans, and the ability to manage quarantine options, giving users flexibility to tailor the program to their preferences and needs.
Furthermore, users have the discretion to choose which utilities to activate, such as the integration of Web Security Guard, allowing them to adapt the programme to their own online browsing habits.
How effective is the program at spyware removal?
Spyware Terminator demonstrates a high degree of efficacy in not only identifying but also successfully removing spyware threats. The software’s removal mechanism is thorough and leaves little to no residue, ensuring a cleaner system post-cleanse.
Moreover, the quarantine feature allows for the safe isolation and storage of suspicious files, which prevents accidental deletion of critical system files, affording users peace of mind.
How do you download Spyware Terminator?
Downloading Spyware Terminator is a straightforward process, simply navigate to the PortalProgramas download website, and click the download link located prominently at the top of the page. This will initiate the download of the latest version of the software, ensuring you are equipped with the latest protective features and updates.
The guided installation process will assist you in setting up the program, and no advanced technical knowledge is required to complete the download and installation. Should any doubt arise, PortalProgramas provides ample instructions and support to guide you.
Is the download process speedy and hassle-free?
Indeed, the download process for Spyware Terminator via PortalProgramas has been optimized for efficiency and simplicity. Users can expect a swift and straightforward download experience, devoid of unnecessary complications or lengthy wait times.
PortalProgramas servers ensure a high download speed, which means that users can commence their protection swiftly following the initiation of the download.
What should users do after downloading Spyware Terminator?
Following the download of Spyware Terminator, users should proceed to install the software by running the downloaded file and following the on-screen instructions. After installation, it is highly recommended to run an initial full system scan to ascertain the current safety status of your device.
Furthermore, exploring the program settings and adjusting them to suit individual protection needs will ensure that Spyware Terminator is fine-tuned for optimal defence right from the start.
Who will benefit most from using it?
Spyware Terminator is a comprehensive solution that caters to a wide range of users. However, it is particularly beneficial for individuals who frequently browse the internet, download files regularly, or those who have previously faced spyware threats and seek a robust, proactive defence system.
Moreover, it’s equally suitable for both technical and non-technical audiences, courtesy of its user-friendly interface and advanced protection features. Business users looking to protect sensitive data will also find it immensely valuable.
FAQ
-
What is the main feature of Spyware Terminator?
-
is Spyware Terminator available for free?
-
Can Spyware Terminator run alongside other antivirus software?
-
Does Spyware Terminator protect against all types of malware?
-
Can Spyware Terminator operate on older versions of Windows?
Ratings about Spyware Terminator
Very good
57 votes
1 review by registered users

(oculto)
2
10
spyware terminator is not an antivirus
15 years ago
Terminator is an antispyware, you have the option to include a virus which I never activated since having one installed is enough. But it's - better, I repeat best-in protection in real-time (as long as you have it configured to do so), you will know what moves in and out of your computer with option of allowing or not (annoying if) but surely, to but when scanning is neither to him, so if the real no time to scan ...
5 votes
Restrictions
Additional details
Latest version
2015
Language
English | Spanish
Total Downloads
7,198
Works with
Windows 2000, XP, Vista, 7
Date
9 years ago
Developer
CRAWLER, LLCSecurity analysis
Trusted